THE INNOVATION: GENERATING ASYMMETRIC STRATEGY
5.1 What Is the Innovation Lab?
The adversarial simulation discovers strategies through iterated play: argument, counter-argument, ruling, adaptation. It operates within conventional legal reasoning boundaries. Lead Counsel argues doctrine; Opposing Counsel attacks it; the Judicial Authority adjudicates it. The result is the best conventional strategy; the dominant move within established rules.
The Innovation Lab asks a different question: what happens when the rules themselves are the vulnerability?
It is a non-adversarial process generating asymmetric strategies—legal arguments that bypass traditional doctrinal boundaries by exploiting logical contradictions, importing reasoning from adjacent fields, reframing factual or legal categories, or using procedural mechanisms for substantive leverage through unconventional channels.
The mechanism operates through four steps:
- Doctrinal constraint relaxation. The system temporarily ignores standard boundaries between legal fields - patent and securities law are not separate silos - and explores how concepts from one domain illuminate or undermine positions in another.
- Logical consistency checking. The system identifies internal contradictions in how doctrines interact. If Principle A holds in Domain X, should it not also hold in Domain Y? If not, why, and can that inconsistency be exploited?
- Recombination. The system assembles novel configurations of existing doctrine, synthesising arguments no single field would generate alone.
- Feasibility assessment. The system evaluates resulting strategies for doctrinal coherence and practical viability; final filtering rests with human counsel.
The Innovation Lab does not play through arguments adversarially but generates candidate strategies for adversarial testing or direct lawyer evaluation. Some outputs are immediately deployable; others are theoretically striking but practically uncertain; a few are brilliant on paper and unworkable in court. This range is a feature. The purpose is to surface possibilities conventional analysis would never reach, leaving judgment about which to pursue with the human advocate.
The label “Move 37” is used advisedly. These are not incremental improvements on orthodox strategy but arguments whose logic only becomes apparent when viewing the problem from an entirely unfamiliar angle; with strategic value, when viable, often decisive.
5.2 The Asymmetric Insights Across All Nine Cases
The Innovation Lab generated dozens of candidate strategies across nine test cases. The most striking are catalogued below, organised by strategic principle rather than case.
A. Logical Annihilation
These strategies defeat opponents by exposing internal contradictions in their position—logical fault lines that, once identified, cannot be repaired without abandoning the theory of the case.
- Case 1.1: Statutory Pre-emption Deletes the Tort. Section 50B’s grant of decompilation rights for interoperability meant there were no “unlawful means”; the conspiracy tort’s core element was retroactively deleted by statute.
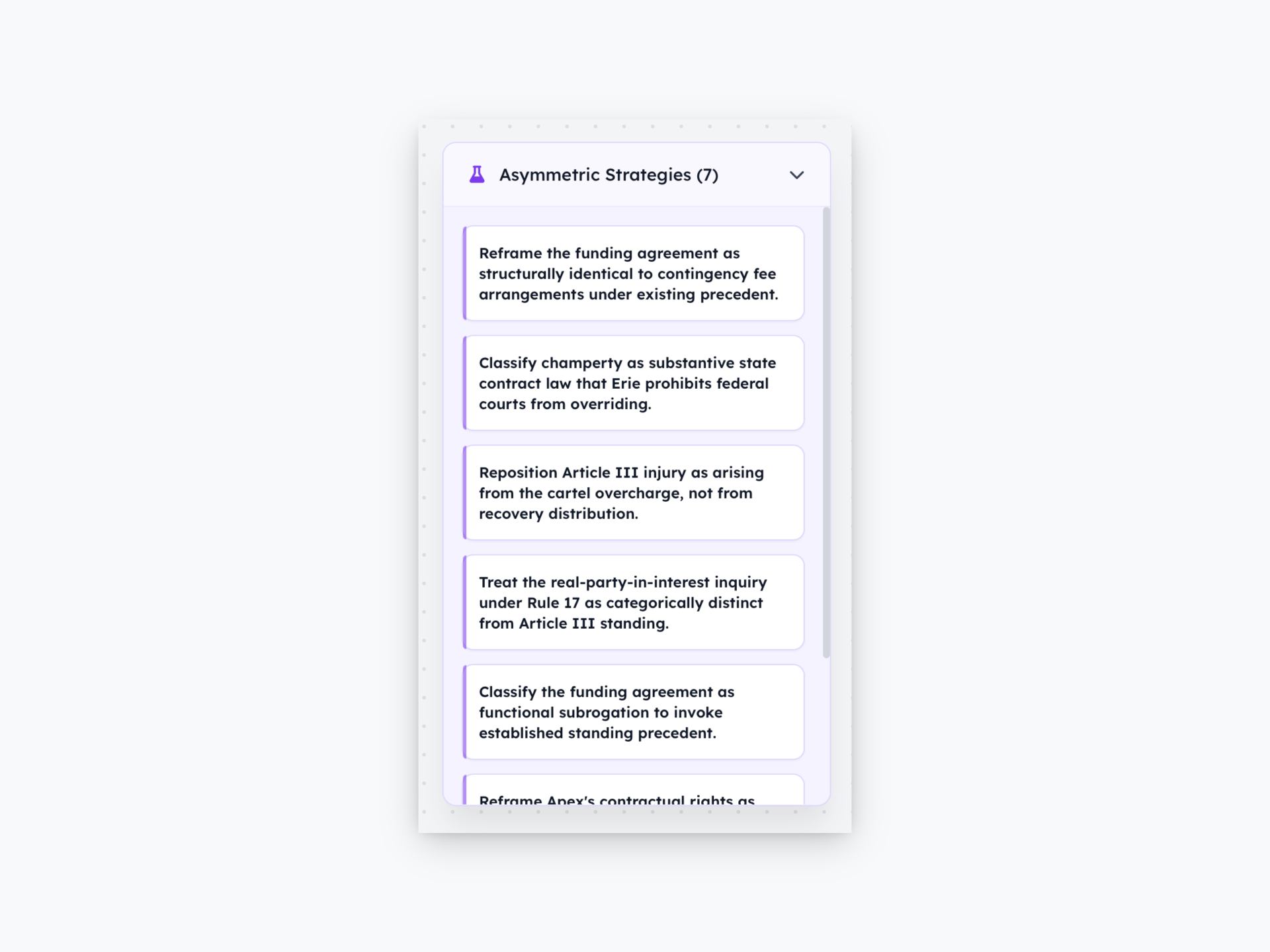
- Case 3.2: Contingency Fee Isomorphism. If litigation funding is champertous because a stranger takes a percentage of recovery, then every contingency fee arrangement involving a lawyer is equally champertous.
- Case 2.2: The Administrative Status Toggle. The misbranding charge rested on a lack of “directions for use” by laypeople, yet prescription status by definition legally precludes safe use by laypeople.
B. Cross-Disciplinary Synthesis
These strategies import reasoning from adjacent legal or analytical fields, generating arguments no single doctrinal silo would produce.
- Case 1.2: Securities Law as Patent Weapon. Securities disclosure obligations regarding licensing strategy created admissions of bad-faith negotiation tactics importable as evidence into the patent dispute.
- Case 1.3: Marginal Consumer Price-Setting Theory. Microeconomic theory dictates that markets are price-set by the marginal consumer; if that consumer paid a premium for an AI label, all consumers suffered identical economic injury.
- Case 3.2: Functional Subrogation from Insurance Law. Litigation funding performs the same economic function as insurance subrogation, which is universally accepted as non-champertous.
- Case 3.3: Standard of Review as Appellate Weapon. Reframing the challenge as legal sufficiency (de novo review) rather than jury instruction error (deferential review) transformed the procedural lens for examining evidence.
C. Ontological Reframing
These strategies change how facts, concepts, or legal categories are classified, shifting them from one doctrinal box to another with transformative consequences.
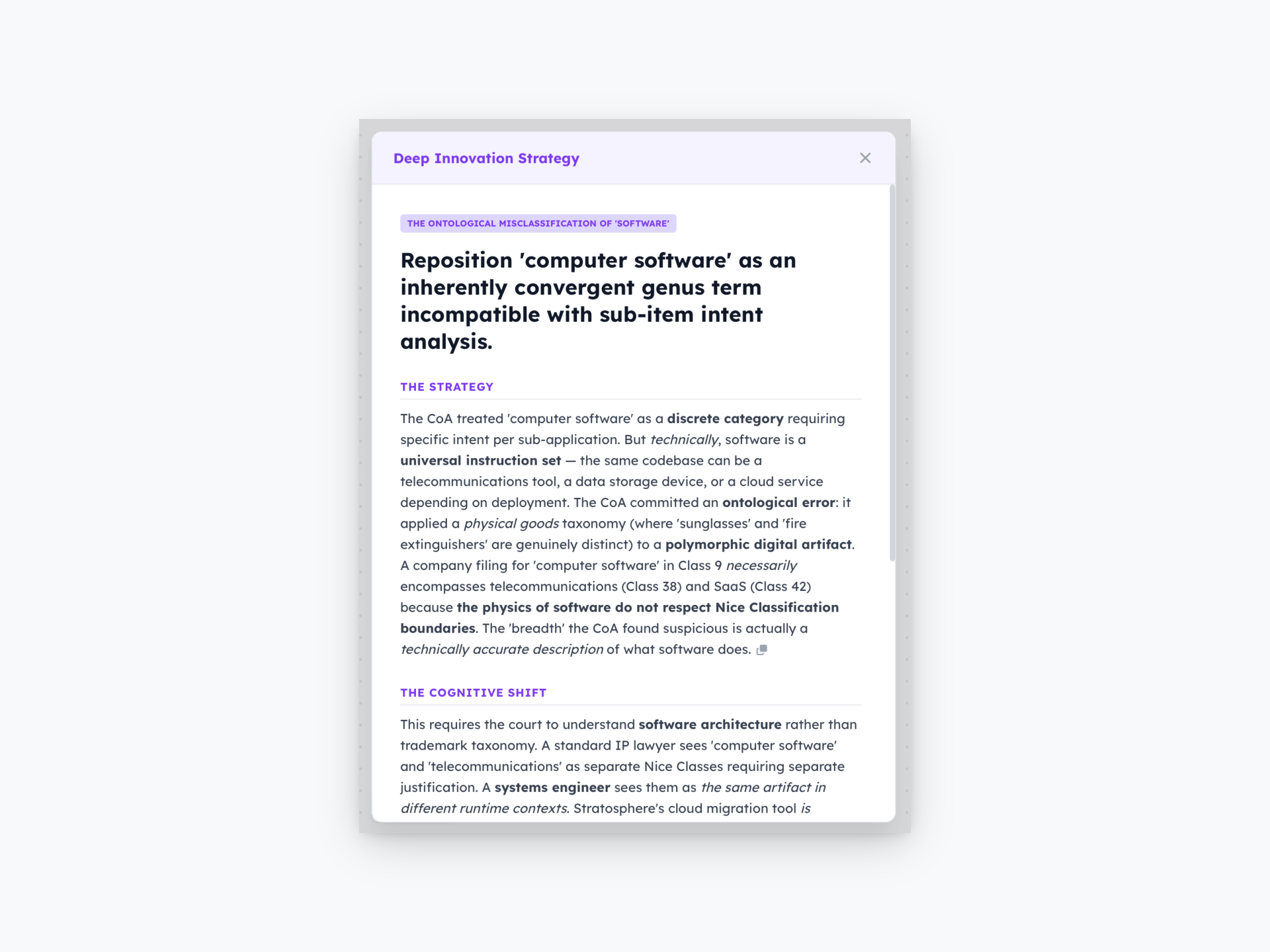
- Case 1.3: AI Label as Economic Signal. Reframing “AI” from a technical specification to an economic price signal shifted the legal focus from factual accuracy to common proof of price inflation.
- Case 2.3: Token as Prepaid Service. Reframing a token as a “prepaid service credit” under the Uniform Commercial Code removes the transaction from the SEC’s “investment contract” jurisdiction.
- Case 2.1: Code Authorship Separated from Code Operation. Separating the act of writing code from the act of operating it shifts jurisdictional liability from the founders to the validators who execute the code.
- Case 3.1: Trademark Breadth as Technical Accuracy. Broad registration in overlapping industries reflects genuine commercial scope and technical accuracy rather than anticompetitive “warehousing” intent.
D. Procedural Flanking
These strategies use procedural rules to achieve substantive leverage through unanticipated channels.
- Case 1.2: Rule 26(d) as Preliminary Injunction Substitute. Expedited discovery under Rule 26(d)(1) achieved the strategic goal of forcing information revelation without the vulnerability of seeking extraordinary injunctive relief.
- Case 2.3: Rule 42(b) Bifurcation as Settlement Lever. Bifurcating liability and damages phases removed prejudicial evidence of investor losses from the initial liability determination, altering settlement calculus.
- Case 3.3: Casteel Indivisibility. Under the doctrine of indivisibility, demonstrating that any one theory in a multi-theory jury charge is legally invalid renders the entire verdict automatically reversible.
E. Information Asymmetry Exploitation
These strategies weaponise opponents’ own conduct or knowledge against their litigation position.
- Case 2.2: Government Knowledge as Evidence of Immateriality. Continued government reimbursement with actual knowledge of alleged fraud serves as “strong evidence” of immateriality under the Escobar standard.
- Case 2.3: The Wu Email as Compliance Evidence. A key prosecution exhibit was reframed as evidence of proactive compliance behaviour—an employee flagging an issue—rather than fraudulent intent.
- Case 2.1: The Transparency Trap. Regulators’ use of public blockchain data to deny disclosure requests created an interpretation asymmetry that could be challenged to regain narrative control.
5.3 Limitations and Failures in the Innovation Lab
Intellectual honesty requires acknowledging that the Innovation Lab does not always produce viable strategies. Some outputs are theoretically elegant but practically unworkable.
Case 2.1: Ethereum Validators as Operators. This argument’s logical structure is sound: if writing code makes someone an “operator,” then validators who actually execute it have stronger claims. As reductio ad absurdum, it exposes the regulator’s control theory incoherence. As litigation strategy, it fails. The argument escalates conflict - threatening the regulatory status of the entire Ethereum network - without providing settlement off-ramps. It is “mutually assured destruction”: theoretically devastating but practically unusable because success consequences are as damaging as failure.
Case 2.1: Smart Contract as Protected Expression. The Innovation Lab generated an argument that blockchain-deployed source code constitutes protected expression under Article 10 of the European Convention on Human Rights. The conceptual foundation is defensible. But the argument is almost certain to fail against countervailing financial crime prevention interests, which courts consistently treat as compelling justification for restricting expression.
These examples illustrate a structural feature rather than a defect. The system explores legal possibility boundaries, sometimes crossing into impracticality. The filtering function - deciding which outputs to pursue - belongs to human counsel. Lawgame is not an oracle but a strategic search engine with unusually wide aperture. Some outputs will be gold; some pyrite. The skill in telling the difference remains human.
5.4 Training Data Implications
The Innovation Lab’s outputs have secondary value extending beyond individual cases.
Each adversarial simulation generates high-quality legal reasoning chains: successful arguments leading to victory, failed arguments with judicial feedback, adversarial exchanges demonstrating effective attack and defence patterns, and judicial reasoning applying doctrine to specific facts. The Innovation Lab adds a layer of cross-domain synthesis and doctrinal contradiction identification unavailable in existing legal datasets.
This corpus - generated through play rather than retrieved from historical records - constitutes a potential fine-tuning dataset for a model specifically trained on litigation strategy rather than generic legal text. Every simulation Lawgame runs improves future outputs because every simulation generates proprietary data competitors cannot access. The adversarial architecture produces strategic recommendations for the case at hand while generating raw material for a reasoning model trained on what matters most in litigation: what works, what does not, and why.